A brand new report reveals how cheap cybercrime can compromise even essentially the most safe organizations. In keeping with Hudson Rock, workers at key US defence entities, together with the Pentagon, main contractors like Lockheed Martin and Honeywell, army branches, and federal companies just like the FBI, have fallen sufferer to Infostealer malware.
These infections expose extremely delicate information, typically for as little as $10, with out the necessity for superior hacking methods as a result of most persistent safety weak point: human error.
How Did It Get Right here?
Infostealer doesn’t depend on flashy exploits or brute power. It performs the lengthy recreation, ready for unsuspecting customers to click on on a malicious hyperlink or obtain one thing they shouldn’t; maybe a recreation mod, pirated software program, or a booby-trapped PDF. As soon as triggered, the malware settles in, harvesting credentials, session cookies, and delicate recordsdata with out elevating any suspicion.
The end result? Cybercriminals can now purchase this stolen information for as little as $10 per contaminated pc on darkish net marketplaces. Want entry to a army VPN? There’s a log for that. Interested by somebody’s e mail inbox? Straightforward. Wish to hijack a session and bypass two-factor authentication? Think about it completed.
And the scope? In keeping with Hudson Rock’s report, over 30 million computer systems worldwide have been hit, with one in 5 holding company credentials. For defence workers, the results couldn’t be extra alarming. Many of those people work on mission-critical tasks involving superior applied sciences like fighter jets, nuclear submarines, and AI techniques. Their compromised gadgets open the door to large-scale information breaches and cyber espionage, not only for their employers however for the nationwide safety of the nation they’re based mostly.
Honeywell and the US Navy: Case Research in Compromise
The report presents particular examples of the injury already completed. At Honeywell, a significant defence contractor, practically 400 workers had been contaminated. This breach uncovered entry to inner techniques, improvement instruments, and, critically, credentials for third-party companions like Microsoft and Cisco.
The U.S. Navy can be affected, with 30 personnel having their credentials stolen. Leaked information consists of entry to e mail techniques, file-sharing platforms, and army coaching sources. These credentials may permit attackers to maneuver laterally via army networks, accessing delicate coaching platforms and even categorized techniques.
This creates a chance for attackers to launch provide chain assaults. The interconnected nature of world provide chains means a single weak hyperlink can result in widespread injury as described by the moral hacker duo final week once they found a vulnerability in a software program provide chain agency that would have had far-reaching penalties if it fell into the mistaken arms.
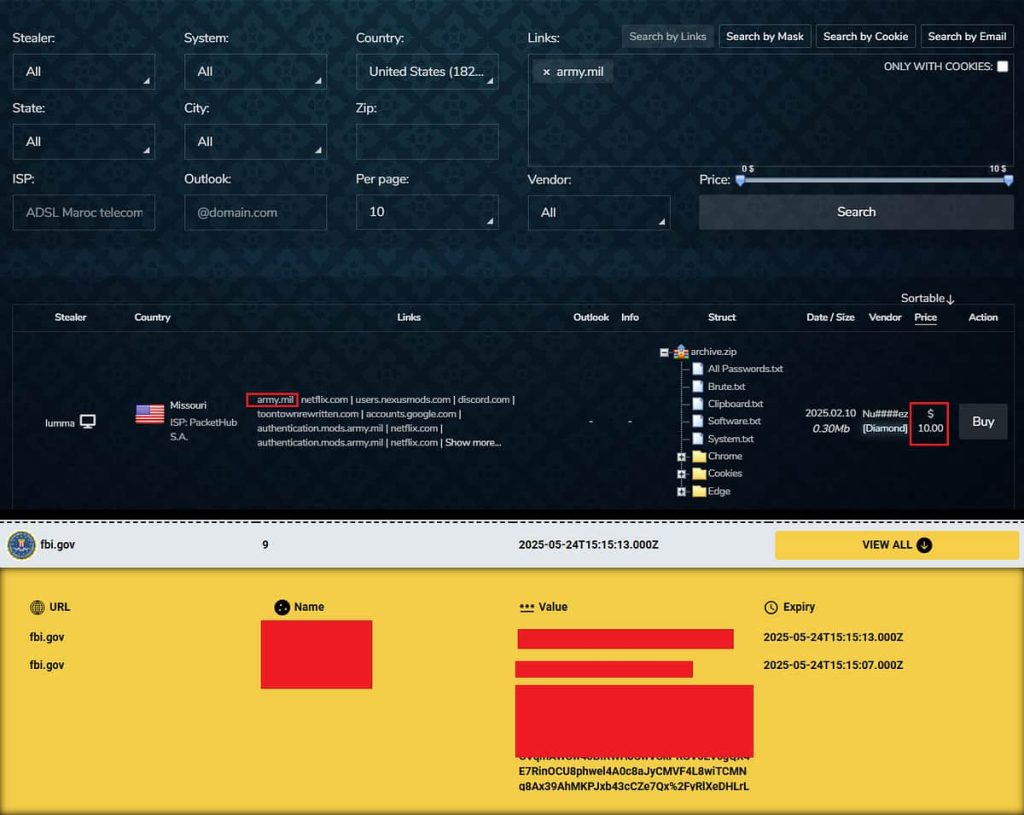
A Wake-Up Name for Nationwide Safety
These findings aren’t simply restricted to the US. The Nationwide Safety of any nation may be jeopardised if infostealers proceed to breach vital infrastructure. With infostealers like Redline, Vidar and Formbook, Fortune 500 firms to small subcontractors, everyone seems to be a possible goal.
Thomas Richards, Director of Community and Pink Workforce Practices at Black Duck, places it bluntly: “The newest report from Hudson Rock is extremely regarding. The stolen information may permit an adversary to infiltrate vital networks and compromise further techniques. Fast motion, together with password resets and forensic investigations, is crucial to mitigate these dangers.”
So what’s subsequent? Hudson Rock’s report proves that cybersecurity is not only about firewalls and superior expertise, additionally it is in regards to the human component demanding a change in focus in the direction of worker cybersecurity coaching.
The extraordinarily low price of those Infostealers makes it clear why regulation enforcement companies worldwide are decided to close down the darkish net and clearnet cybercrime markets. Nonetheless, cybersecurity isn’t a checkbox; it’s a mindset. And if there’s one factor this report makes clear, it’s that the time to behave is now.