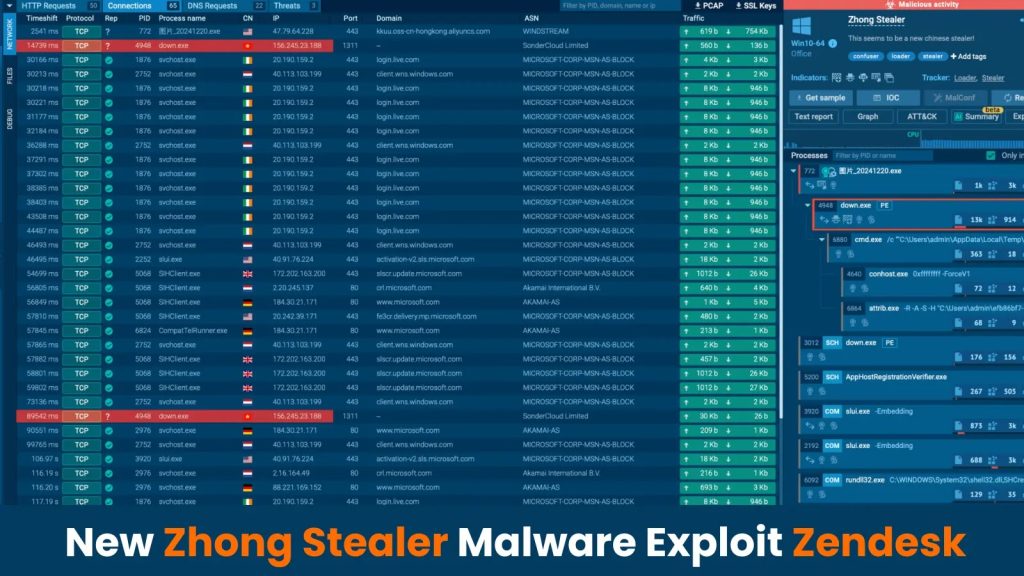
A newly recognized malware, dubbed Zhong Stealer, has emerged as a big menace to the fintech and cryptocurrency sectors.
Any.run researchers found zhong malware throughout a phishing marketing campaign between December 20 and 24, 2024, the malware exploits buyer assist platforms like Zendesk to infiltrate organizations.
The attackers masquerade as prospects, leveraging social engineering techniques to trick assist brokers into downloading malicious recordsdata.
Exploitation through Zendesk
The assault begins with the creation of fraudulent assist tickets by attackers utilizing newly registered accounts.
These tickets usually embrace poorly written messages in Chinese language and ZIP file attachments claiming to comprise screenshots or further particulars.
The ZIP recordsdata, named in Simplified or Conventional Chinese language characters, conceal executable (.exe) recordsdata that provoke the malware upon opening.


As soon as executed, Zhong Stealer connects to a command-and-control (C2) server hosted in Hong Kong.
The malware downloads further parts, together with a downloader disguised as a professional BitDefender Safety updater, utilizing a stolen however revoked digital certificates.


This misleading method permits the malware to bypass preliminary detection mechanisms successfully.
You may submit suspicious recordsdata and URLs to ANY.RUN for proactive evaluation of threats concentrating on your organization - Attempt for Free
Superior Methods for Persistence
Zhong Stealer employs a number of techniques to ascertain persistence on compromised methods.
It modifies Home windows registry keys and schedules duties through Activity Scheduler to make sure it runs at startup, even after system reboots.
Moreover, it disables safety occasion logging to evade detection throughout forensic evaluation.
The malware conducts reconnaissance by querying system properties comparable to language settings, hostnames, and proxy configurations.
It additionally scans browser extensions and saved credentials from widespread browsers like Courageous and Edge/Web Explorer.
As soon as delicate knowledge is harvested, Zhong exfiltrates it to its C2 server over non-standard community ports like port 1131, additional complicating detection efforts.
The Zhong Stealer marketing campaign underscores the rising sophistication of cyber threats concentrating on fintech and cryptocurrency corporations.
By exploiting human vulnerabilities by way of buyer assist platforms, attackers bypass conventional safety measures.
The malware’s capability to steal credentials and delicate knowledge poses extreme dangers for organizations dealing with monetary transactions and digital belongings.
To defend in opposition to threats like Zhong Stealer, organizations should undertake proactive cybersecurity measures:
- Practice buyer assist groups to acknowledge phishing makes an attempt and keep away from opening suspicious attachments.
- Implement zero-trust safety insurance policies to limit file execution from unverified sources.
- Monitor community visitors for uncommon exercise, significantly connections to non-standard ports related to C2 servers.
- Make the most of superior malware evaluation instruments like ANY.RUN’s Interactive Sandbox for real-time menace detection and behavioral evaluation.
The Zhong Stealer incident highlights the vital want for vigilance in cybersecurity practices throughout the fintech and cryptocurrency sectors.
By combining technical defenses with worker coaching, organizations can mitigate the dangers posed by evolving malware campaigns like this one.
Free Webinar: Higher SOC with Interactive Malware Sandbox for Incident Response, and Risk Searching - Register Right here




