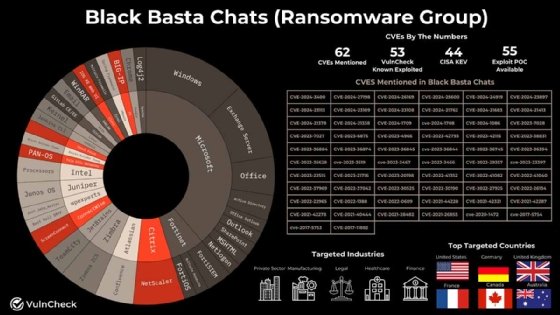
Leaked chat logs from the Black Basta ransomware gang reference 62 CVEs, together with greater than 50 identified exploited vulnerabilities, in line with analysis printed Monday by safety vendor VulnCheck.
VulnCheck’s analysis follows a leak of chat logs belonging to Black Basta, a Russian-speaking ransomware-as-a-service (RaaS) gang that emerged in 2022 and has focused essential sectors reminiscent of healthcare. VulnCheck, a risk and vulnerability intelligence vendor, analyzed the Black Basta chats and recognized 62 distinctive CVEs that have been mentioned amongst members of the RaaS operation.
Of the 62 talked about within the analysis, 44 are current in CISA’s Identified Exploited Vulnerabilities catalog, and 53 are in VulnCheck’s personal KEV.
“Black Basta reveals a transparent choice for targets with identified weaknesses, specializing in vulnerabilities that have already got out there exploits,” VulnCheck safety researcher Patrick Garrity wrote within the weblog publish.
Garrity additionally mentioned the gang seems to favor “broadly adopted enterprise applied sciences,” together with these supplied by Microsoft, Cisco, Citrix, Fortinet, Palo Alto Networks, Test Level Software program Applied sciences and Atlassian. He famous that mentions of particular CVEs don’t essentially imply Black Basta used them in assaults.
Some notable vulnerabilities mentioned within the chat logs embrace the 2020 Home windows escalation of privilege flaw referred to as “Zerologon,” CVE-2020-1472; a Home windows Search distant code execution zero-day vulnerability, CVE-2023-36884; two FortiSIEM vulnerabilities with 10 CVSS scores, CVE-2024-23109 and CVE-2024-23108; a number of Microsoft Trade vulnerabilities together with ProxyNotShell bugs CVE-2022-41040 and CVE-2022-41082; and the Meltdown and Spectre Intel flaws CVE-2017-5754 and CVE-2017-5753 (respectively).
Garrity mentioned Black Basta would focus on new vulnerabilities inside a number of days of safety advisories changing into out there. Along with utilizing identified exploits, the gang would focus on buying exploits from rising teams “with hesitancy.” Furthermore, Garrity mentioned, “there may be proof suggesting that Black Basta has the assets to develop new exploits.”
“The evaluation of Black Basta’s chat logs reveals a methodical but opportunistic strategy that focuses on well-known vulnerabilities and high-value targets,” Garrity wrote. “Whereas the group leverages established exploit frameworks and available instruments, their discussions additionally counsel potential for brand new exploit improvement and tactical shifts. For defenders, the important thing takeaway is to prioritize the remediation of vulnerabilities utilizing an evidence-based strategy.”
In an e mail, Garrity instructed Informa TechTarget that Black Basta’s techniques, methods and procedures have been according to different ransomware teams. “The analysis reveals that these actors are opportunistic and transfer quick, concentrating on preliminary entry, Microsoft applied sciences and e mail providers,” he mentioned.
Alexander Culafi is a senior data safety information author and podcast host for Informa TechTarget.