Late in January 2025, a Managed Service Supplier (MSP) administrator obtained a well-crafted phishing e-mail containing what gave the impression to be an authentication alert for his or her ScreenConnect Distant Monitoring and Administration (RMM) instrument. That e-mail resulted in Qilin ransomware actors getting access to the administrator’s credentials—and launching ransomware assaults on the MSP’s prospects.
Sophos MDR’s risk Intelligence crew assesses with excessive confidence that this incident might be attributed to a ransomware affiliate whose exercise is tracked by Sophos as STAC4365. The assault used comparable infrastructure, area naming patterns, strategies, instruments, and practices to these utilized in different phishing campaigns Sophos MDR risk intelligence discovered relationship again to late 2022. These makes an attempt leveraged phishing websites constructed with the evilginx open-source adversary-in-the-middle assault framework to gather credentials and session cookies and bypass multi-factor authentication (MFA).
On this case, as in others tied to this risk cluster, the attackers used faux ScreenConnect domains to behave as proxies to the precise ScreenConnect login course of. As soon as the administrator clicked on the login hyperlink on the e-mail to overview the authentication, they had been redirected to a malicious phishing website, cloud.screenconnect[.]com.ms, that masqueraded because the legit ScreenConnect login web page. As soon as they entered their credentials into the faux ScreenConnect website, the attackers had been in a position to intercept these inputs. Sophos believes the faux ScreenConnect website proxied the inputs again to the legit ScreenConnect website to confirm the credentials and seize the time-based one-time password (TOTP) despatched from ScreenConnect to the administrator by e-mail.
After intercepting the MFA inputs, the attacker efficiently authenticated to the legit ScreenConnect Cloud portal utilizing the administrator’s tremendous administrator account. This granted them permission to successfully do something inside this ScreenConnect occasion and led to an assault deploying Qilin.
Background: Qilin
Qilin is a Ransomware-as-a-Service program that has been in operation since 2022, beforehand working underneath the title “Agenda.” The Qilin group recruits associates on Russian-language cybercrime boards. In line with Microsoft Menace Intelligence, these associates have grown this 12 months to incorporate a North Korean state actor labeled by Microsoft as “Moonstone Sleet.”
Qilin ransomware makes use of a data-leak website hosted on Tor to use strain on victims being extorted. In Might of 2024, that strain was expanded to the open web when risk actors related to Qilin ransomware launched a data-leak website named “WikiLeaksV2.” This challenge was hosted at an IP handle supplied by a Russian Web service supplier that has been tied to command-and-control (C2) exercise, malware internet hosting, and phishing actions prior to now. The positioning stays lively and was linked within the ransom notes left on this incident.
Determine 2: The Qilin data-leak website hosted on Tor incorporates a QR code and hyperlink to the WikiLeaksV2 web page
Background: STAC4365
STAC4365 is related to a sample of actions and indicators held in widespread by a bunch of phishing websites relationship again to November 2022. These websites shared traits equivalent to URL path and website construction, and the domains related to them have targeted on spoofing legit ScreenConnect URLs.

| Area | Earliest Exercise |
| account.microsoftonline.com[.]ec | February 2025 |
| cloud.screenconnect.com[.]ms | January 2025 |
| cloud.screenconnect[.]is | November 2024 |
| cloud.screenconnect.com[.]so | October 2024 |
| cloud.screenconnect.com[.]bo | July 2024 |
| cloud.screenconnect.com[.]cm | July 2024 |
| cloud.screenconnect.com[.]am | April 2024 |
| cloud.screenconnect.com[.]ly | February 2024 |
| cloud.screenconect[.]com[.]mx | January 2024 |
| cloud.screenconnect[.]co[.]za | January 2024 |
| cloud.screenconnect[.]uk[.]com | January 2024 |
| cloud.screenconnect[.]de[.]com | November 2023 |
| cloud.screenconnect.com[.]se | October 2023 |
| cloud.screenconnect.jpn[.]com | October 2023 |
| cloud.screenconnect.com[.]ng | June 2023 |
| cloud.screenconnect.com[.]ph | Might 2023 |
| cloud.screenconnect.com[.]vc | Might 2023 |
| cloud.screenconnect[.]cl | April 2023 |
| cloud.screenconnect[.]gr[.]com | April 2023 |
| cloud.screenconect[.]eu | January 2023 |
| cloud.screenconnect[.]co[.]com | January 2023 |
| cloud.screenconnect[.]us[.]com | January 2023 |
| cloud.iscreenconnect[.]com | December 2022 |
| cloud.screenconnect[.]app | November 2022 |
Determine 4: A listing of domains matching STAC4365’s sample of exercise
To provision these phishing websites, STAC4365 leverages evilginx, an open-source adversary-in-the-middle assault framework used for phishing credentials and session cookies and performing as an MFA relay.

Evilginx2, the most recent model, features a “javascriptRedirect” function that risk actors use to selectively route visitors. STAC4365 leverages awstrack[.]me together with JavaScript redirects to make sure that solely focused victims, accessing the phishing website by way of the supposed monitoring hyperlink, attain the credential-harvesting web page – whereas these visiting straight (equivalent to researchers) are redirected to the legit service portal, evading detection and evaluation. This function is widespread in different MFA phishing platforms, as demonstrated by Rockstar and FlowerStorm.
STAC4365 Qilin assault chain
Preliminary entry
The phishing lure particularly focused the MSP’s administrator account, and precisely mimicked a ConnectWise ScreenConnect login alert:
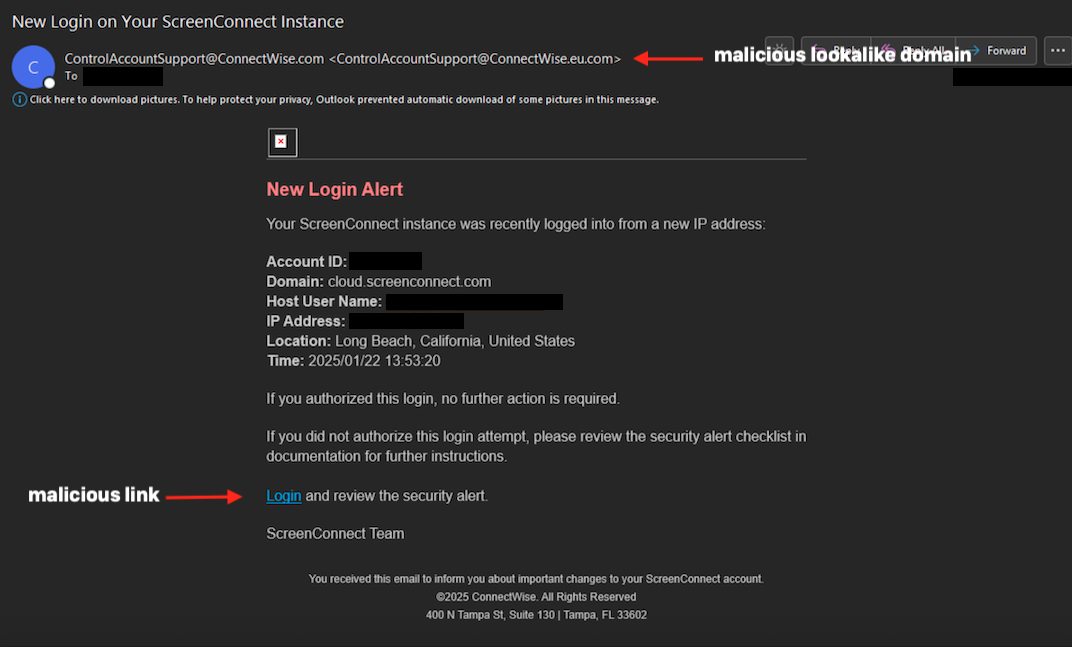
The focused administrator clicked the “Login and overview the safety alert” hyperlink, which took the sufferer’s browser to the phishing web page by way of a malicious redirect utilizing Amazon Easy Electronic mail Service (SES):
hxxps[:]//b8dymnk3.r.us-east-1.awstrack[.]me/L0/https[:]%2Fpercent2Fcloud.screenconnect[.]com.mspercent2FsuKcHZYV/1/010001948f5ca748-c4d2fc4f-aa9e-40d4-afe9-bbe0036bc608-000000/mWU0NBS5qVoIVdXUd4HdKWrsBSI=410
The redirected hyperlink resolved to the URI of a ScreenConnect-mimicking area:
hxxps[:]//cloud.screenconnect[.]com.ms/suKcHZYV/1/010001948f5ca748-c4d2fc4f-aa9e-40d4-afe9-bbe0036bc608-000000/mWU0NBS5qVoIVdXUd4HdKWrsBSI=410
This URI was used to confirm the goal; different visits to the area had been redirected to the legit cloud.screenconnect.com. The host at cloud.screenconnect[.]com.ms (186.2.163[.]10) was seemingly configured as a reverse proxy to the legit ScreenConnect area.
Utilizing the intercepted credentials and the MFA code, the attacker logged into the goal’s ScreenConnect subdomain via the ScreenConnect Management Panel and gained entry to the MSP’s distant administration atmosphere.
Persistence, Command and Management
Shortly after efficiently authenticating into the ScreenConnect atmosphere because the tremendous administrator account, the attacker pushed out a brand new ScreenConnect occasion utilizing a file named ‘ru.msi,’ which put in an attacker-managed ScreenConnect occasion throughout a number of of the MSP’s managed prospects.

Discovery, credential entry and lateral motion
The malicious ScreenConnect occasion was utilized in a number of buyer environments to carry out community enumeration and consumer discovery and reset quite a few consumer account credentials. The attackers additionally used the ScreenConnect occasion to variety of legit instruments to realize entry to extra native credentials and execute distant instructions, in addition to utilized Home windows instruments, together with:
- PsExec
- exe (NetExec from GitHub)
- WinRM
- ScreenConnect occasion
Moreover, the actors downloaded a file named “veeam.exe,” an executable coded to take advantage of CVE-2023-27532, a vulnerability in the Veeam Cloud Backup service which permits an unauthenticated consumer to request unencrypted credentials from the native Veeam configuration database. This file’s title, path location, and SHA256 hash are an identical to one reported by Huntress in a 2023 cyberattack that additionally leveraged ScreenConnect however didn’t lead to ransomware deployment.
Assortment
Following the invention and lateral motion phases, the attacker started double extortion efforts by leveraging the accounts they modified credentials for, executing WinRAR to gather information throughout a number of buyer environments.

Exfiltration
As soon as the attackers collected information using WinRAR, they exfiltrated the .rar information to easyupload.io by way of an Incognito tab in Google Chrome.
Protection evasion and affect
All through the incident, the attackers utilized numerous protection evasion strategies to clear their tracks. When accessing EasyUpload by way of Google Chrome, they utilized Incognito mode to cover forensic information. In addition they eliminated instruments after execution equivalent to WinRAR.
Utilizing the malicious ScreenConnect occasion, the attacker made certain to establish and goal backups at a number of buyer areas to stop restoration of providers and to raised guarantee their ransom calls for had been met. Moreover, they modified numerous boot choices to make sure that the focused units would boot into Protected Mode with networking.
Lastly, they leveraged the compromised accounts to deploy Qilin ransomware throughout a number of prospects’ environments.
SophosLabs analyzed the ransomware binary retrieved by the MDR crew. It contained the next performance:
- Cease and disable Quantity Shadow Copy Service (VSS) service
- Allow symbolic hyperlinks
- Enumerate hosts
- Delete shadow copies
- Delete Home windows Occasion Logs
- Set wallpaper to ransomware message
- Delete itself after execution
Whereas a number of buyer environments had been impacted by the identical ransomware binary, every buyer had their very own distinctive 32-character password related to the execution of the ransomware binary.
Word the completely different finish of the redacted passwords within the screenshot under:
Moreover, the readme information dropped by the ransomware had distinctive chat IDs for every buyer, indicating that the risk actor knew they had been concentrating on completely different organizations and prospects.

Suggestions for defenders
MSPs rely extensively on exterior software program and providers to meet their operational duties for buyer organizations. Ransomware operators goal these providers for a similar purpose—they’ve grow to be an more and more widespread vector for downstream assaults on MSP prospects. So it will be important for MSPs and organizations of all sizes that make the most of these providers to grasp the chance elements related to them and take steps to mitigate them.
Attackers with legitimate administrative credentials and entry are troublesome to cease, notably in the case of the exfiltration of information. However there are measures organizations can take to stop the preliminary compromise of key credentials, and to Impede execution of ransomware..
Preliminary entry on this case was gained via focused phishing and interception of an MFA TOTP. The attackers used a lookalike area and a well-crafted e-mail to get the goal to click on on the hyperlink. Defenders ought to incorporate assessments into organizational phishing coaching to assist customers spot lookalike and different suspicious domains. Moreover, guarantee your e-mail answer both flags or blocks incoming messages that fail to go a Area-based Message Authentication, Reporting and Conformance (DMARC) examine.
The phishing assault on this case used an AITM phishing package to relay credentials and a TOTP to acquire a legitimate session. When doable, organizations ought to restrict entry to company purposes and third-party providers to recognized managed gadgets via conditional entry, and migrate to phishing-resistant authentication providers (equivalent to these primarily based on FIDO 2).
On this assault, the actor configured techniques to reboot in protected mode to bypass endpoint safety protections. Organizations ought to deploy safety towards protected boot restarts with out endpoint safety. Sophos prospects can do that by enabling lively assault enhancements in Sophos Central via Endpoint and Server Menace Safety insurance policies.
Indicators of compromise for STAC4365 and Qilin are supplied on the Sophos GitHub web page right here.