
Ransomware has grow to be a favourite assault technique for dangerous actors, with reviews labeling it the best method for cybercriminals to monetize unlawful entry into networks. Information of ransomware assaults seems each day.
Extra troubling nonetheless are predictions that ransomware gangs have gotten more proficient at utilizing AI, and well-funded ones might quickly use agentic AI to launch much more refined assaults at scale.
Such advances present how far the world has come from the primary ransomware assault again in 1989, when hundreds of the World Well being Group’s AIDS Convention attendees returned dwelling to seek out floppy disks of their mailboxes that allegedly held a questionnaire in regards to the chance of contracting HIV. However they did not discover any questions: The disks contained a program designed to encrypt the names of their pc recordsdata. In the event that they needed their recordsdata restored, they have been advised to ship $189 to a Panamanian submit workplace field.
Quick-forward a couple of years to see the evolution of ransomware, enabled by the rise of the web, society’s shift to an interconnected digital world and the introduction of cryptocurrency. Malicious actors organized. Ransomware as a service (RaaS) emerged. Double and triple extortion assaults turned widespread.
Consequently, the variety of victims, the sum of money demanded and the affect of profitable assaults have soared through the years.
Information on the variety of ransomware assaults, estimated ransom funds and the whole prices incurred by victims varies from one report back to the following. As a result of victims are generally reluctant to publicly share that they have been hit by ransomware, whether or not they paid a ransom or how a lot they spent to get well from such an incident, an correct estimate of the harm is troublesome to find out.
Research, nevertheless, do level to some troubling numbers. For instance, NCC Group counted 5,263 ransomware instances in 2024, noting in its “2024 Cyber Menace Monitor Report” that the tally is the very best quantity in annual instances for the reason that cybersecurity software program and companies firm began monitoring ransomware exercise in 2021. In “The State of Ransomware 2024,” safety vendor Sophos estimated that 59% of organizations have been hit by some sort of ransomware incident within the prior yr.
Quantifying the largest assaults might be troublesome, however some stand out. The next is a listing of 15 of probably the most impactful ransomware assaults up to now, ordered alphabetically.
1. Ascension
Sort of ransomware: Black Basta ransomware
Attacker: Reportedly Black Basta
Date: Might 8, 2024
Losses: $1.3 billion
Ascension, a St. Louis-based Catholic well being system, mentioned it had been hit by ransomware that disrupted its entry to digital well being information, telecommunications methods and a few vital operational methods, together with ones used for affected person care. Ascension was pressured to divert ambulances and shut pharmacies, whereas its clinicians reported that the incident affected their potential to look after sufferers. Moreover, the assault uncovered the private data of 5.6 million people and price the nonprofit system a reported $1.3 billion. It’s unclear whether or not Ascension paid a ransom as a part of its remediation and restoration efforts.
2. Caesars and MGM casinos
Sort of ransomware: Assault on NCR Aloha POS platform
Attacker: ALPHV/BlackCat
Date: September 2023
Losses: Upward of $100 million
Caesars and MGM, two of the largest and most recognizable U.S. lodge and on line casino chains, fell sufferer to ransomware assaults launched by the ALPHV/BlackCat group. The assaults on Caesars and MGM stemmed from a bigger assault on the NCR Aloha point-of-sale platform, which was extensively used within the hospitality business. Each Caesars and MGM misplaced entry to their total IT infrastructure, together with slot machines. In response to cybersecurity firm Kaspersky, Caesars paid a $15 million ransom, which was half the demanded quantity, whereas MGM didn’t pay a ransom, opting to revive its methods at a value of $10 million and struggling a lack of $100 million through the nine-day restoration time.
3. CDK International
Sort of ransomware: Not reported
Attacker: BlackSuit
Date: June 8, 2024
Losses: $1 billion-plus collectively along with a reported ransom fee of $25 million value of bitcoin
The assault on CDK International led to widespread system outages at 15,000 U.S. and Canadian auto dealerships, halting their potential to trace stock, schedule companies and course of gross sales. The preliminary assault, believed to come back from the BlackSuit ransomware gang, was adopted by a second assault whereas CDK International was working to get well its methods. The assault price auto dealerships greater than $1 billion collectively, in keeping with an estimate from consulting agency Anderson Financial Group.
4. Change Healthcare/UnitedHealth Group
Sort of ransomware: Exploitation of a Citrix portal account
Attacker: ALPHV/BlackCat
Date: Feb. 21, 2024
Losses: Greater than $800 million in direct damages, together with a $22 million ransom, and estimated total prices of roughly $2.5 billion
ALPHV/BlackCat launched a profitable ransomware assault on Change Healthcare, a division of UnitedHealth Group. The attackers, who gained entry by exploiting a Citrix portal account that lacked multifactor authentication, spent 9 days stealing information as they moved undetected inside the firm’s methods. They then hit the corporate with a ransomware assault that disrupted greater than 100 functions, ensuing within the lack of ability for healthcare entities nationwide to course of digital funds and medical claims. The incident is the most important healthcare breach within the U.S. up to now, affecting greater than 100 million folks. It price the corporate greater than $800 million in direct prices, together with a $22 million ransom fee made in cryptocurrency. Complete prices from the assault have been an estimated $2.5 billion to $3 billion.
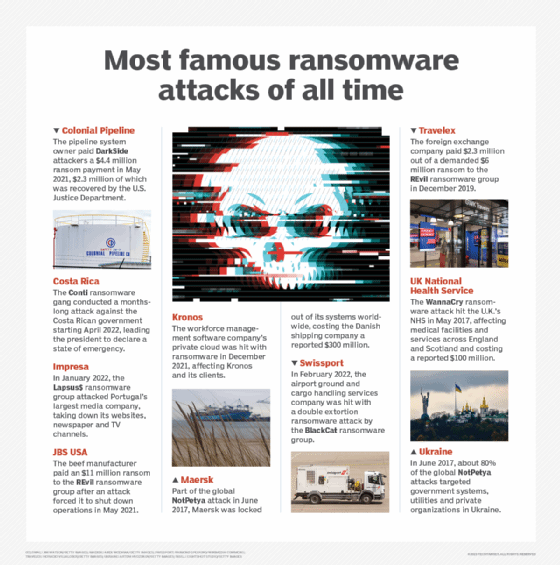
5. Colonial Pipeline
Sort of ransomware: DarkSide RaaS
Attacker: DarkSide
Date: Might 7, 2021
Losses: $4.4 million (roughly $2.3 million was recovered)
The assault on Colonial Pipeline turned one of the infamous ransomware assaults due to its affect on on a regular basis Individuals, with these residing in Southeast states immediately dealing with gasoline provide shortages.
Colonial Pipeline, proprietor of a pipeline system carrying gas from Texas to the Southeast, suffered a ransomware assault on the pc methods that managed the pipeline. DarkSide attackers accessed the methods by means of a compromised credential for a legacy VPN. Working with the FBI, the corporate paid a $4.4 million ransom inside hours of the assault. The affect lasted for days, nevertheless, as the corporate struggled to completely restore operations.
Federal and state officers, together with then-President Joe Biden, issued emergency declarations within the days after the assault to make sure gas might attain the affected area and restrict damages. The assault additionally led Biden to problem an govt order to enhance the nation’s cybersecurity.
The U.S. Division of Justice later introduced it had seized $2.3 million of the $4.4 million in bitcoin used to pay the ransom.
6. Costa Rica
Sort of ransomware: Conti
Attacker: Conti gang
Date: April 17, 2022
Losses: $30 million a day
The Conti ransomware gang launched a monthslong assault towards Costa Rican authorities establishments. The preliminary assault on the Ministry of Finance used compromised credentials to put in malware. The Costa Rican Ministry of Science, Innovation, Know-how and Telecommunications and the Ministry of Labor and Social Safety have been later attacked. The federal government shut down a number of methods, leading to delayed authorities funds, slowed and halted commerce, and restricted companies.
Inside the first week of the assault, then-President Carlos Alvarado refused to pay the purported $10 million ransom. The Conti ransomware gang then leaked virtually all of the 672 GB of knowledge it stole through the assaults. It took months earlier than methods have been restored — however not earlier than the nation’s newly elected president, Rodrigo Chaves Robles, declared a state of emergency.
7. Impresa
Sort of ransomware: Lapsus$
Attacker: Lapsus$
Date: Jan. 1, 2022
Losses: Not reported
Ransomware group Lapsus$ launched one of many world’s most conspicuous ransomware assaults when it struck Impresa, Portugal’s largest media conglomerate. The assault took down all its web sites, its weekly newspaper and its TV channels. Attackers additionally gained management of the corporate’s Twitter account and claimed it had entry to the corporate’s AWS account. In response to information reviews, Impresa confirmed the assault however mentioned no ransom demand was made.
Lapsus$, which had attacked Brazil’s Ministry of Well being in 2021, posted a ransom message that threatened to launch firm information. Portuguese authorities labeled the Impresa assault the most important cyberattack within the nation’s historical past.
8. JBS USA
Sort of ransomware: REvil RaaS
Attacker: REvil
Date: Might 30, 2021
Losses: $11 million ransom fee
Beef producer JBS USA Holdings Inc. paid an $11 million ransom in bitcoin to malicious actors after an assault pressured it to close down operations. IT staffers initially observed issues with among the firm’s servers, and shortly thereafter, the corporate obtained a message demanding a ransom. Pilgrim’s Pleasure Corp., a unit of JBS, was additionally affected by the assault. Operations have been restored inside days, however not earlier than JBS made the hefty fee.
9. Kronos
Sort of ransomware: Not reported
Attacker: Not reported
Date: Dec. 11, 2021
Losses: Along with a reported ransom fee, Kronos paid $6 million in 2023 to settle a class-action lawsuit filed by Kronos purchasers who alleged the corporate did not do sufficient to guard its methods.
Final Kronos Group, a workforce administration software program maker doing enterprise in additional than 100 international locations, was hit by a ransomware assault on its personal cloud. The incident affected prospects across the globe, spawned yearslong ripple results and uncovered an earlier breach that magnified the affect.
The assault uncovered worker information for lots of the firm’s enterprise purchasers. Consequently, these purchasers confronted interruptions, delays and errors in issuing paychecks to their employees.
The Kronos assault raised questions on vendor accountability and highlighted the significance of third-party danger administration, as organizations acknowledged that assaults on their enterprise companions might have an effect on them as nicely.
10. Maersk
Sort of ransomware: NotPetya
Attacker: Russian-backed hackers suspected within the assault
Date: June 27, 2017
Losses: Roughly $300 million
Danish transport big A.P. Moller-Maersk suffered roughly $300 million in losses after it was hit as a part of the worldwide NotPetya assaults. The malware, which exploited the EternalBlue Home windows vulnerability and unfold by means of a backdoor within the professional monetary software program MeDoc, locked the corporate out of the methods it used to function transport terminals all around the world. As wiperware, NotPetya was designed to inflict most harm by not solely encrypting all recordsdata on contaminated computer systems but in addition utterly wiping or rewriting them so they might not be recovered — even by means of decryption. It took Maersk two weeks to get well its pc operations.
11. Swissport
Sort of ransomware: BlackCat RaaS
Attacker: BlackCat
Date: Feb. 3, 2022
Losses: Air service disruptions; no monetary information reported
Swissport, a Swiss firm offering airport ground- and cargo-handling companies, introduced that its methods had been hit by a ransomware assault in 2022. The incident delayed a small variety of flights, however Swissport mentioned it had contained the incident inside 24 hours. Ransomware group BlackCat, nevertheless, quickly indicated it had not solely encrypted the corporate’s recordsdata but in addition had stolen 1.6 TB of Swissport information it was trying to promote in a basic instance of a double extortion assault.
12. Synnovis/U.Okay. Nationwide Well being Service
Sort of ransomware: Not reported
Attacker: Qilin
Date: June 3, 2024
Losses: £33 million
Synnovis, a pathology and laboratory companies supplier to the U.Okay.’s Nationwide Well being Service (NHS), fell sufferer to a ransomware assault launched by the cybercriminal group Qilin. The assault encrypted Synnovis’ IT methods, creating important disruptions to affected person healthcare — specifically, cancelled and postponed procedures, blood transfusions, exams and outpatient appointments. It additionally pressured healthcare suppliers to revert to handbook and paper-based methods to course of data. The assault uncovered the information of practically 1 million NHS sufferers, with the attackers stealing and ultimately leaking 400 GB value of delicate information when Synnovis didn’t pay the demanded $50 million ransom.
13. Travelex
Sort of ransomware: REvil RaaS
Attacker: REvil
Date: Dec. 31, 2019
Losses: $2.3 million ransom paid; firm pressured into administration in 2020 partially as a result of assault
On the time it was hit by the REvil ransomware gang, Travelex was the world’s largest overseas trade bureau. Attackers focused a identified vulnerability in Pulse Safe VPN servers to infiltrate the corporate’s methods and encrypt 5 GB of knowledge. They demanded a $6 million ransom, which was negotiated all the way down to $2.3 million.
The assault took down the corporate’s inside methods for practically two weeks. The monetary fallout was so extreme that it finally pressured the corporate into administration in 2020.
14. U.Okay. Nationwide Well being Service
Sort of ransomware: WannaCry
Attacker: Linked to North Korea
Date: Might 2017
Losses: £92 million (roughly $100 million)
Firms around the globe felt the affect of the WannaCry ransomware assault, the primary ransomware to take advantage of the EternalBlue flaw in Home windows methods.
The U.Okay.’s NHS was one of the outstanding WannaCry victims, with a number of hospitals, common practitioners and pharmacies affected in England and Scotland. NHS amenities have been pressured to delay and divert medical companies.
15. Ukraine
Sort of ransomware: NotPetya
Attacker: Russia’s GRU navy spy company named as attacker, in keeping with the CIA
Date: June 27, 2017
Losses: Estimated at $10 billion globally
Whereas greater than 60 international locations have been affected, the preliminary international NotPetya assaults in 2017 primarily focused victims in France, Germany and Ukraine, the latter of which sustained about 80% of the assaults, in keeping with researchers from cybersecurity software program firm ESET. The nation’s pc methods have been affected, in addition to networks operated by personal firms and electrical utilities. The aforementioned Maersk ransomware assault was additionally a part of this collection of assaults.
Mary Okay. Pratt is an award-winning freelance journalist with a deal with masking enterprise IT and cybersecurity administration.





