
Cybersecurity researchers have unearthed a complicated assault leveraging AutoIT, a long-standing scripting language recognized for its deep integration with Home windows working techniques.
Typically in comparison with .NET for its persistence in malicious campaigns, AutoIT’s simplicity and skill to work together with Home windows elements make it a popular software amongst cybercriminals.
This weekend, a very intricate malware supply mechanism was recognized, that includes a double-layered AutoIT script designed to deploy a doubtlessly devastating payload.
Multi-Layered AutoIT Malware Marketing campaign
The assault begins with an executable named “1. Challenge & Revenue.exe” (SHA256: b5fbae9376db12a3fcbc99e83ccad97c87fb9e23370152d1452768a3676f5aeb), a compiled AutoIT script that serves because the preliminary an infection vector.
Upon decompilation, the script reveals a simple but malicious intent.
It defines key variables pointing to suspicious URLs and native file paths, akin to a obtain hyperlink for a secondary AutoIT interpreter saved as “C:UsersPublicGuard.exe” and a PowerShell script, “PublicProfile.ps1,” which is generated and executed to facilitate additional an infection.
Moreover, one other AutoIT script is retrieved and saved as “Safe.au3” in the identical listing, hinting at a multi-stage deployment technique.
The malware ensures persistence by making a .url file within the Home windows Startup listing, which triggers a JavaScript file to re-execute the AutoIT interpreter with a second-layer script named “G.”
From Executable to C2 Communication
Delving into the second layer, the “G” script stands out for its obfuscation methods.
Strings inside the code are encoded utilizing a customized perform dubbed “Wales,” which transforms ASCII values right into a readable format solely after decoding with a selected key.
A Python implementation of the Wales perform reveals hidden references, akin to checks for antivirus processes like “avastui.exe,” suggesting an try and evade detection.
This obfuscation underscores the attackers’ efforts to hide their true intentions whereas interacting with system processes.
The assault culminates within the execution of “jsc.exe,” a authentic Home windows element, which is hijacked to load a malicious DLL named “Urshqbgpm.dll.”

This closing payload is injected into the method, enabling covert operations on the compromised system.
Additional evaluation of the DLL reveals robust ties to AsyncRAT, a infamous distant entry trojan, as evidenced by tried connections to a command-and-control (C2) server at 139[.]99[.]188[.]124 on port 56001, a recognized indicator of AsyncRAT exercise.
Intriguingly, the DLL additionally incorporates quite a few references to PureHVNC, a lesser-known however equally harmful framework usually related to hidden digital community computing capabilities, permitting attackers to realize Graphical Person Interface entry to victims’ machines remotely.
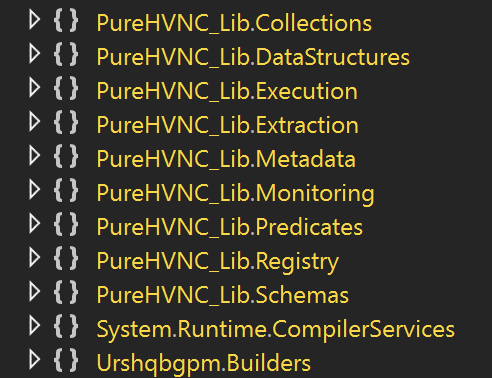
Whereas the precise nature of the malware stays below investigation, the mix of those parts factors to a extremely focused and chronic menace designed to keep up long-term entry to contaminated techniques.
This incident highlights the enduring enchantment of AutoIT within the malware panorama, as its capability to mix seamlessly with authentic Home windows processes continues to problem detection mechanisms.
Cybersecurity professionals are urged to stay vigilant, monitor for suspicious AutoIT executables, and scrutinize community visitors for connections to recognized malicious IPs.
As attackers refine their multi-layered approaches, understanding and mitigating such threats turns into paramount to safeguarding Home windows environments from compromise.
Discover this Information Fascinating! Comply with us on Google Information, LinkedIn, & X to Get Instantaneous Updates!
.png
)




