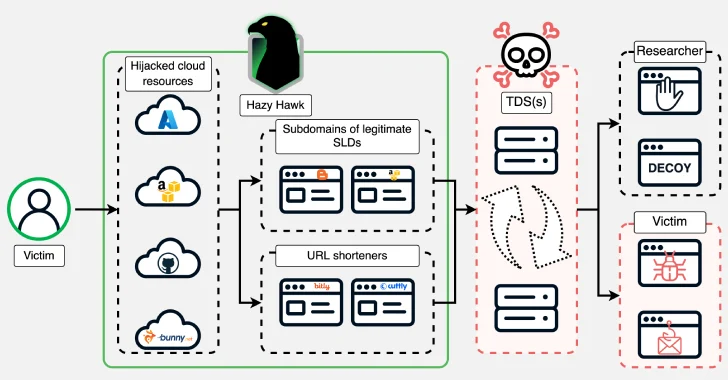
A menace actor generally known as Hazy Hawk has been noticed hijacking deserted cloud sources of high-profile organizations, together with Amazon S3 buckets and Microsoft Azure endpoints, by leveraging misconfigurations within the Area Identify System (DNS) data.
The hijacked domains are then used to host URLs that direct customers to scams and malware by way of visitors distribution programs (TDSes), in line with Infoblox. A few of the different sources usurped by the menace actor embrace these hosted on Akamai, Bunny CDN, Cloudflare CDN, GitHub, and Netlify.
The DNS menace intelligence agency stated it first found the menace actor after it gained management of a number of sub-domains related to the U.S. Heart for Illness Management (CDC) in February 2025.
It has since been decided that different authorities businesses throughout the globe, outstanding universities, and worldwide companies corresponding to Deloitte, PricewaterhouseCoopers, and Ernst & Younger have been victimized by the identical menace actor since not less than December 2023.
“Maybe essentially the most exceptional factor about Hazy Hawk is that these hard-to-discover, weak domains with ties to esteemed organizations usually are not getting used for espionage or ‘intellectual’ cybercrime,” Infoblox’s Jacques Portal and Renée Burton stated in a report shared with The Hacker Information.
“As a substitute, they feed into the seedy underworld of adtech, whisking victims to a variety of scams and pretend functions, and utilizing browser notifications to set off processes that may have a lingering impression.”
What makes Hazy Hawk’s operations noteworthy is the hijacking of trusted and respected domains belonging to respectable organizations, thus boosting their credibility in search outcomes when they’re getting used to serve malicious and spammy content material. However much more concerningly, the strategy allows the menace actors to bypass detection.
Underpinning the operation is the flexibility of the attackers to grab management of deserted domains with dangling DNS CNAME data, a way beforehand uncovered by Guardio in early 2024 as being exploited by dangerous actors for spam proliferation and click on monetization. All a menace actor must do is register the lacking useful resource to hijack the area.
Hazy Hawk goes a step additional by discovering deserted cloud sources after which commandeering them for malicious functions. In some circumstances, the menace actor employs URL redirection methods to hide which cloud useful resource was hijacked.
“We use the identify Hazy Hawk for this actor due to how they discover and hijack cloud sources which have dangling DNS CNAME data after which use them in malicious URL distribution,” Infoblox stated. “It is attainable that the area hijacking part is supplied as a service and is utilized by a gaggle of actors.”
The assault chains usually contain cloning the content material of respectable websites for his or her preliminary website hosted on the hijacked domains, whereas luring victims into visiting them with pornographic or pirated content material. The location guests are then funneled by way of a TDS to find out the place they land subsequent.
“Hazy Hawk is likely one of the dozens of menace actors we observe throughout the promoting affiliate world,” the corporate stated. “Menace actors who belong to affiliate promoting packages drive customers into tailor-made malicious content material and are incentivized to incorporate requests to permit push notifications from ‘web sites’ alongside the redirection path.”
In doing so, the concept is to flood a sufferer’s machine with push notifications and ship an limitless torrent of malicious content material, with every notification resulting in totally different scams, scareware, and pretend surveys, and accompanied by requests to permit extra push notifications.
To forestall and shield in opposition to Hazy Hawk actions, area homeowners are really helpful to take away a DNS CNAME report as quickly as a useful resource is shut down. Finish customers, alternatively, are suggested to disclaim notification requests from web sites they do not know.
“Whereas operators like Hazy Hawk are chargeable for the preliminary lure, the person who clicks is led right into a labyrinth of sketchy and outright malicious adtech. The truth that Hazy Hawk places appreciable effort into finding weak domains after which utilizing them for rip-off operations reveals that these promoting affiliate packages are profitable sufficient to pay nicely,” Infoblox stated.









