A threat register is a doc that data a corporation’s dangers, together with details about the likelihood of these dangers affecting the enterprise, their doubtless influence, whether or not and the way the group will handle every threat, and the proprietor of every threat.
Organizational leaders use a threat register to get a holistic view of their dangers and their responses. Having this data in a single place serves two functions: to extra successfully handle total threat to the enterprise and to extra successfully talk their threat place and mitigation methods to stakeholders, together with the complete govt group, board of administrators, auditors, buyers, companions and staff.
“A threat register is principally for accountability. It is a device of threat administration,” defined Martin Grace, professor and school director of the Vaughan Institute for Danger Administration and Insurance coverage on the College of Iowa’s Tippie Faculty of Enterprise.
Completely different ranges of threat registers
A threat register’s degree of element and class varies primarily based on a corporation’s trade, measurement and degree of threat administration maturity. Small corporations typically use a spreadsheet to trace dangers and their deliberate responses to them. International corporations, public corporations and corporations in regulated industries akin to finance or healthcare — all of which face more and more advanced dangers and should report back to extra entities — usually use extra refined laptop functions for his or her threat registers.
Terminology
A threat register is typically known as a threat log, RAID (dangers, actions, points and choices) log, threat administration plan or threat stock. Some additionally use the time period threat matrix; nonetheless, a threat matrix, which plots a threat’s precedence together with the criticality of the asset in danger, is often a part of a threat register.
Why do you have to use a threat register?
Organizations of each variety, from governmental businesses to nonprofits to the worldwide giants, have at all times needed to take care of dangers.
Nonetheless, organizations right now typically face increasingly more advanced dangers than their counterparts from the previous. Present enterprise dangers embrace risky financial circumstances, quickly altering geopolitical insurance policies, cyberthreats, expertise shortages, third-party vulnerabilities and disruptive innovation.
Consequently, organizations want a scientific strategy to view the totality of their dangers and responses.
A well-constructed and well-maintained threat register provides executives, board members, auditors and different stakeholders the visibility they want into the group’s threat place, together with reassurance that its threat administration plan does the next:
- Identifies the group’s high dangers.
- Assesses every threat’s likelihood and potential influence.
- Devises responses that align with each the group’s threat urge for food and its threat tolerance.
- Allocates sources to response efforts that align with the potential severity of every threat.
- Assigns accountability for every threat to make sure accountability for response actions.
Moreover, organizations can use a threat register to trace threat response actions and spending, which, in flip, may help executives establish methods to turn into extra environment friendly and efficient of their threat administration processes.
Organizations can consider a threat register as their monitoring system, mentioned Sarah Lynn, a companion at assurance and advisory agency BPM.
“It tracks each threat, and it tracks what you decide to do,” she mentioned, including that “if you do not know what the dangers are, individuals will make errors or do what they assume is best to do.”
Moreover, some organizations are required by regulatory authorities to have a threat register. Others are required to have one as a way to conduct enterprise with sure companions or in sure trade sectors. For instance, a cloud firm looking for to do enterprise with the federal authorities should be compliant with the Federal Danger and Authorization Administration Program (FedRAMP), which requires a complete threat administration program.
As well as, buyers and regulators typically require corporations to take care of a threat register, seeing it as an illustration of a mature threat administration technique.
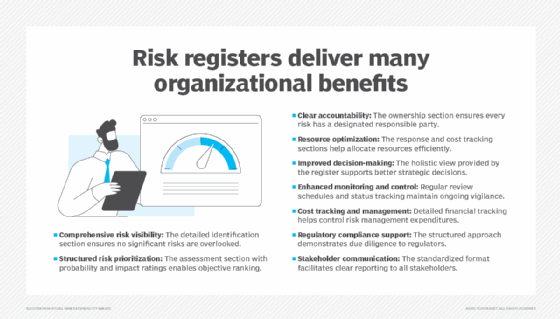
Advantages of threat registers
The existence of a threat register in a corporation typically produces the next advantages:
- Visibility and transparency. As beforehand famous, a threat register offers a holistic view of the important thing dangers going through the group, together with assessments of every threat and deliberate response.
- Correct prioritization of dangers and response actions. That consolidated view of enterprise dangers provides executives and threat leaders the flexibility to successfully rank dangers and prioritize response actions to make sure they’re allocating essentially the most sources to these dangers that warrant it.
- Accountability. Likewise, that holistic view allows executives to make sure that every threat is assigned to an proprietor.
- Enhanced decision-making. Executives, stakeholders and enterprise leaders liable for dangers have the data they should make simpler choices and to make these choices extra shortly utilizing a threat register than in the event that they needed to search out and piece collectively siloed threat data.
- Alignment and understanding of dangers all through the group. Executives, managers and threat leaders can use the chance register to share data with staff in any respect ranges of the group, leveraging the visibility supplied by the register to construct alignment and buy-in.
- Improved adherence to threat administration methods. That alignment and buy-in usually results in higher adherence to the group’s threat administration program as a result of individuals perceive why threat discount insurance policies exist and the way these insurance policies defend the group and people.
- Regulatory compliance assist. Equally, that alignment and buy-in imply higher compliance with laws, not simply inner threat administration insurance policies.
- Lowered prices for the chance administration program. As a result of the chance register helps organizations prioritize dangers and responses, they’re simpler of their spending. For instance, a threat register might assist an organization perceive whether or not it wants a classy fireplace suppression system or only a few fireplace extinguishers to adequately handle its threat of fireside.
Challenges of utilizing a threat register
Though enterprise leaders typically acknowledge the significance of getting a threat register, many wrestle with creating and utilizing this device. That is not stunning, contemplating the a number of challenges that come together with devising and sustaining a threat register.
The primary problem is figuring out the dangers that ought to go onto the chance register. It is a balancing act as the chance register ought to give a holistic view of threat however not be slowed down with minutia on each potential threat.
“The danger register is used to rank the dangers, give that overarching view and perspective,” mentioned Caitlin Holmes, senior managing director at FTI Consulting. “You do not wish to be overzealous.”
As soon as dangers are recognized, executives face one other problem: evaluating and ranking every threat primarily based on its likelihood and potential influence on the group.
One other massive problem is definitely utilizing the chance register. The danger register shouldn’t be a check-the-box exercise, nor a guidelines of to-do, one-and-done objects. Fairly, it’s meant to be consulted, built-in into the chance administration program and up to date as actions occur and dangers evolve. If all that does not occur, then the funding into growing a threat register may very well be wasted.
“You do not need a threat register to be only a guidelines of belongings you did. That is meaningless,” Grace mentioned. “Its goal is meaningless should you don’t have a monitoring part, if it is not actively reviewed month-to-month or quarterly.”
What’s included in a threat register?
A number of threat register templates exist, and plenty of company software program applications — notably these for governance, threat and compliance — have threat register parts. Registers usually present fields for the next data:
- The danger itself, together with a novel identifier akin to a reputation or code.
- An outline of the chance, with concise supporting particulars.
- The danger’s class (e.g., strategic, operational, course of, monetary, technical, and many others.).
- Every threat’s likelihood or probability of prevalence.
- Data on the influence of the chance, ought to it happen.
- Particulars on the criticality of the asset affected by the chance.
- A precedence rating to know how shortly a threat should be addressed.
- A threat rating, which is commonly listed numerically on a 1-to-3 or 1-to-5 scale, or generally as red-yellow-green.
- A response plan on whether or not to just accept, switch, mitigate or eradicate the chance and a abstract of tips on how to accomplish the deliberate response.
- The proprietor of every threat.
- Standing stories.
- Area to report any extra related data.
“The ultimate factor is you wish to hold monitor of how a lot time and {dollars} are spent on every threat,” Grace added.
Easy methods to create a threat register
Writing an efficient threat register is a collaborative effort in all however the smallest corporations. It ought to contain executives, threat professionals and, in some instances, line-of-business leaders, and maybe even frontline staff.
At a excessive degree, these groups ought to take the next actions:
- Decide whether or not the chance register is for the entire group, a selected division or a selected challenge.
- Determine, describe and classify the dangers.
- Assess every threat for the probability of prevalence and the potential severity of that prevalence.
- Assign a ranking to every threat.
- Prioritize dangers primarily based on their probability and influence to give attention to essentially the most important ones.
- Craft a response plan for every threat.
- Assign an proprietor to every threat.
- Set up an proprietor of the general threat register to make sure the register is used to tell threat administration actions and to replace the chance register on an ongoing foundation.
Conclusion
The danger register is a key part of a profitable threat administration technique — supplied it’s seen as a dwelling doc that modifications as typically as dangers do, so it could actually successfully information organizational leaders on risk-related choices.
When used as a part of a threat administration program, a threat register pays massive dividends, enabling leaders to anticipate dangers whereas minimizing the price of doing so. That, in flip, helps the group succeed, even because it contends with the quite a few, advanced dangers which are always altering round it.
“A threat register provides the overarching view of the [organization’s] threat place,” Holmes mentioned, “and it permits management to be extra proactive in managing it, which means they will have to make use of much less sources to cope with threat, and they are often simpler in doing so.”
Mary Okay. Pratt is an award-winning freelance journalist with a give attention to overlaying enterprise IT and cybersecurity administration.