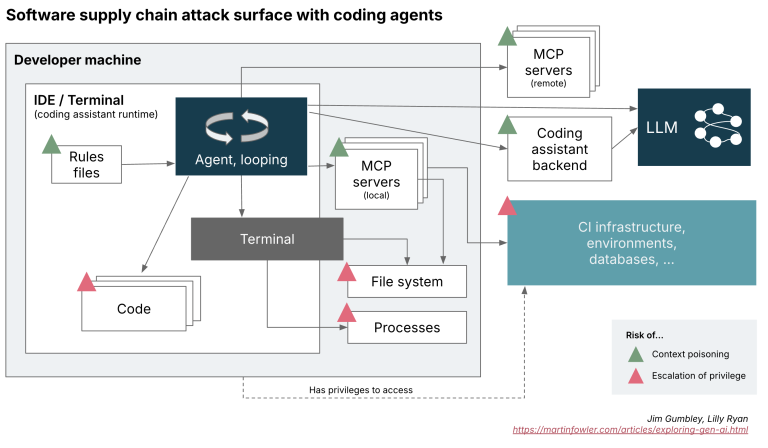
We’ve lengthy acknowledged that developer environments signify a weak level within the software program provide chain. Builders,...
Year: 2025
Cybersecurity researchers have unearthed a complicated assault leveraging AutoIT, a long-standing scripting language recognized for its deep...
Beginning in July, MIT’s Shaping the Way forward for Work Initiative within the Division of Economics will...
Patch administration is without doubt one of the oldest and most well-known IT and safety duties,...
The Mannequin Context Protocol (MCP) represents a strong paradigm shift in how massive language fashions work together...
The Disconnect That’s Costing You: The place Knowledge Silos Cripple Operational Effectivity Within the age of...
Construct Customized AI Brokers for Workflow Automation Construct Customized AI Brokers for Workflow Automation to remove repetitive...
ESET reviews on RoundPress, a cyber espionage marketing campaign by Russia’s Fancy Bear (Sednit) focusing on Ukraine-related...
Frontend growth shapes consumer experiences and ensures seamless interplay with net purposes. As net applied sciences evolve,...
Possibly it’s the nighttime. Possibly you’re not in search of something severe — only a cheeky chat,...