Cybersecurity researchers from SafeBreach Labs have revealed new vulnerabilities in Google’s Fast Share file-transfer utility for Home windows, together with a vital flaw that enables attackers to execute code on focused units.
The findings, disclosed this week, spotlight dangers within the broadly used instrument—even after Google patched earlier points reported in 2024.
The QuickShell Exploit Chain
Initially offered at DEF CON 32 (2024), the “QuickShell” analysis uncovered 10 vulnerabilities in Fast Share, a cross-platform instrument for transferring information between Android, Home windows, and ChromeOS units.
The utility employs Bluetooth, Wi-Fi Direct, and different protocols to allow peer-to-peer sharing.
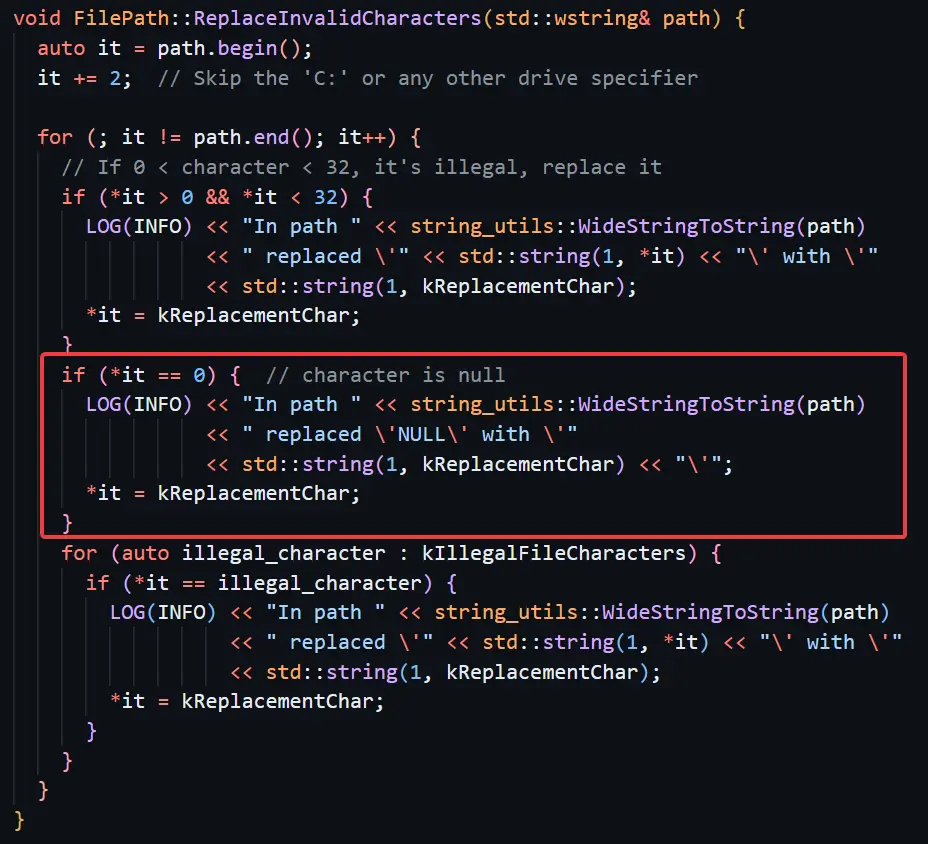

Researchers Shir Tamari and Shmuel Cohen found that attackers may chain these flaws to attain distant code execution (RCE) on Home windows programs, enabling full system takeover.
Key weaknesses included:
- Unauthorized file writes (CVE-2024-38272)
- Listing traversal exploits
- A number of denial-of-service (DoS) vulnerabilities
Google addressed these flaws in early 2024, however follow-up assessments revealed gaps within the fixes.
Patch Bypass: New Assault Vector Emerges
In August 2024, SafeBreach researchers revisited the patched vulnerabilities and recognized two vital oversights:
- Incomplete DoS Repair
A vulnerability inflicting crashes by way of invalid UTF-8 filenames (e.g., x00FileName) was solely partially resolved. Google blocked filenames beginning with null terminators, however researchers bypassed this through the use of different invalid UTF-8 sequences (e.g., xc5xffFileName), crashing the appliance. - Unauthorized File Write Bypass
The unique exploit (CVE-2024-38272) allowed sending information with out person consent. Google’s repair auto-deleted “unknown” information post-transfer. Nonetheless, researchers discovered that sending two information with similar payload IDs tricked Fast Share into deleting just one, leaving the second malicious file within the person’s Downloads folder.
Google addressed the brand new flaws in late 2024, assigning CVE-2024-10668 to the file-write bypass. Patches have been rolled out by way of computerized updates.
“This case underscores the challenges of securing advanced, protocol-diverse purposes,” stated Tamari. “Whereas Google responded swiftly, layered defenses and rigorous patch verification are important.”
Implications for Customers
Fast Ship pre-installs on newer Home windows PCs amplify dangers. Customers are urged to:
- Guarantee Fast Share is up to date to the most recent model.
- Disable the instrument if unused.
- Keep away from accepting information from untrusted units.
The findings spotlight broader classes for multi-protocol software program—notably instruments bridging cell and desktop ecosystems. As Tamari famous, “Attackers will all the time search gaps in logic. Defenders should assume like them.”
Discover this Information Fascinating! Observe us on Google Information, LinkedIn, & X to Get Instantaneous Updates!