A brand new phishing marketing campaign is concentrating on customers throughout Latin America, and on the middle of it’s Grandoreiro, a banking trojan recognized for stealing delicate monetary knowledge. With geofencing and stealthy evasion ways, this malware is proving troublesome to catch with customary defenses.
Let’s take a better have a look at the marketing campaign, how the assault unfolds, and what makes it so efficient.
Grandoreiro Assault Overview
Between February 19 and March 14, researchers observed a surge in phishing exercise tied to Grandoreiro, and indicators present the marketing campaign continues to be ongoing.
Grandoreiro has been round for years, continually evolving to remain forward of detection. It’s designed to steal banking credentials, monitor person exercise, and grant distant entry to attackers.
One of many standout strategies on this marketing campaign is geofencing. Earlier than operating, the malware checks the sufferer’s IP deal with to find out their location. If the person isn’t in a focused Latin American nation, the malware merely stops executing. This makes the marketing campaign extra centered, reduces pointless publicity, and helps it slip previous international safety monitoring.
Grandoreiro Assault Chain
Grandoreiro is thought for slipping previous conventional safety instruments, making it powerful to detect utilizing automated options alone. Nonetheless, with the assistance of interactive sandboxes, it’s doable to watch the malware’s full habits in actual time.
Right here’s a whole have a look at the execution chain inside a safe sandbox:
View sandbox evaluation session
Understanding the who, when, and the way behind this marketing campaign will assist safety groups proactively strengthen their defenses. Actual-time menace evaluation platforms not solely uncover these particulars but additionally make them instantly actionable.
Preliminary Entry: Phishing Electronic mail
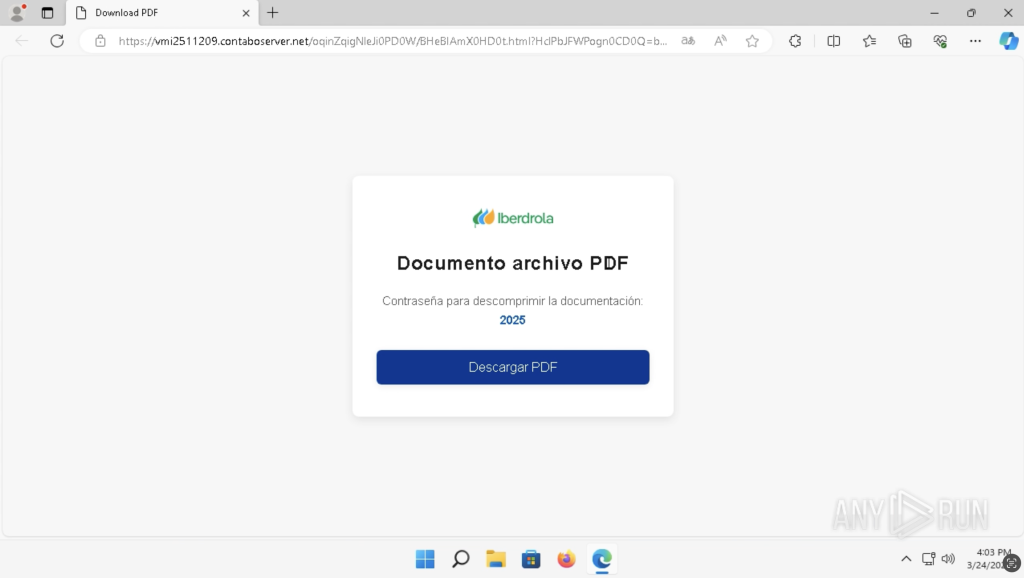
The an infection begins with a phishing web page that lures the sufferer into clicking a hyperlink or downloading a pretend PDF doc. As a substitute of a PDF, the file is definitely a compressed archive (.ZIP or .RAR) containing the Grandoreiro loader.
Execution & Geofencing
As soon as the file is extracted and opened, the malware sends a request to ip-apicom to find out the person’s geolocation.
If the IP deal with falls outdoors the focused LATAM nations, the malware halts execution, but when it matches a focused area, the assault proceeds.
DNS Evasion: Google DNS
Grandoreiro avoids native DNS queries by sending a request to dns.google. It offers the area identify of its command-and-control (C2) server, which Google resolves to an IP deal with.
This step helps it bypass DNS-based blocking mechanisms and improves its probabilities of profitable communication.
Conventional options typically miss these evasion methods, however ANY.RUN captures them in actual time, serving to groups construct efficient detection logic that truly displays how trendy malware behaves.
Connection to C2
After resolving the C2 area, the malware sends a GET request to the retrieved IP deal with to determine a connection. This opens the door for the attacker to ship further payloads, steal credentials, or take distant management of the contaminated machine.
Grandoreiro in Motion: Ways & Methods
Establishing a connection to the C2 server is only the start. As soon as communication is profitable, Grandoreiro kicks off a collection of actions designed to remain hidden, collect knowledge, and put together for additional exploitation.
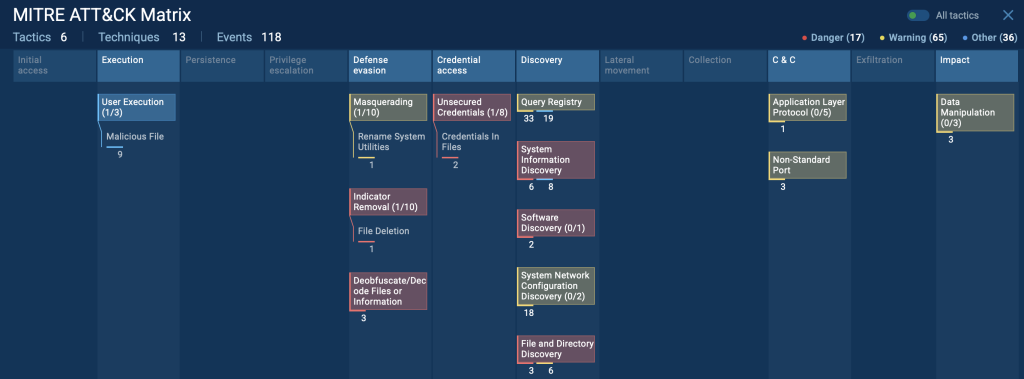
On this particular assault, ANY.RUN’s sandbox reveals a variety of strategies triggered throughout a number of MITRE ATT&CK classes. You may see all of them mapped within the ATT&CK tab of the evaluation session:
Detection & Response Ideas
Detecting Grandoreiro isn’t straightforward; it blends in effectively and makes use of intelligent methods. However right here’s how one can keep one step forward:
- Look ahead to phishing lures posing as PDF downloads (typically .ZIP or .RAR archives).
- Monitor exterior DNS requests, particularly to
dns.google, proper after execution.
- Flag geolocation lookups to providers like ip-apicom; it’s a key a part of Grandoreiro’s filtering tactic.
- Use behavior-based evaluation to catch post-execution ways like file deletion, credential entry, or system discovery.
Catch the Assault Earlier than It Spreads
The Grandoreiro marketing campaign reveals how trendy threats evolve and why visibility into habits issues greater than ever.
With ANY.RUN sandbox, safety groups can work together with malware in actual time, uncover hidden ways, and reply with confidence. From phishing to post-exploitation, all the pieces is mapped, visualized, and prepared for motion.