In a current discovery by the CYFIRMA analysis staff, a complicated malware marketing campaign dubbed Odyssey Stealer has been uncovered, concentrating on macOS customers via a misleading technique generally known as Clickfix ways.
This marketing campaign leverages typosquatted domains malicious web sites mimicking reliable ones just like the macOS App Retailer, finance platforms, or cryptocurrency information portals to trick customers into executing dangerous AppleScripts (osascripts).

These scripts are engineered to reap delicate information, together with browser cookies, saved passwords, cryptocurrency pockets info, and browser extensions, posing a extreme risk to people, significantly these engaged in monetary and crypto actions.
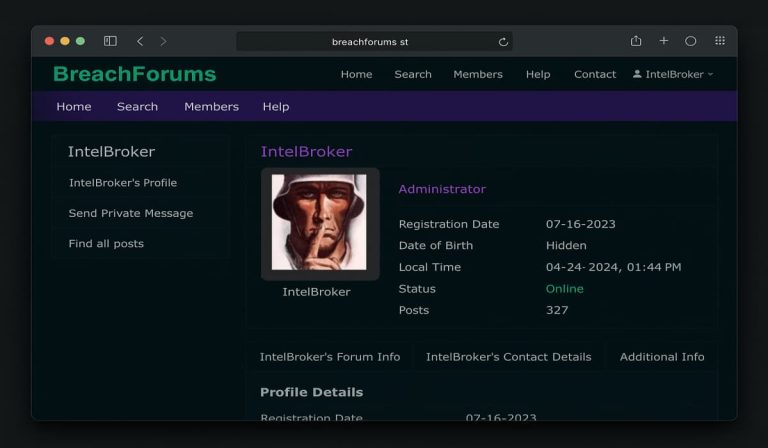
Odyssey Stealer Targets macOS Customers
The operation, linked to a command-and-control (C2) panel primarily hosted in Russia, showcases a professional-grade information theft mechanism that prioritizes Western customers in the USA and the European Union whereas avoiding victims in CIS international locations, a sample typically related to Russian-aligned cybercriminal teams.
The Clickfix method begins with the creation of visually comparable or typosquatted domains designed to use consumer typing errors.
Upon visiting these malicious websites, customers are greeted with a pretend Cloudflare-style CAPTCHA immediate, accompanied by directions to repeat and paste a Base64-encoded command into their terminal.
In accordance with Cyfirma, this command fetches and executes a non-obfuscated osascript from servers like odyssey1[.]to or particular IP addresses, triggering a cascade of malicious actions.

Finance and Crypto Fans at Excessive Danger
The script creates a short lived listing, reminiscent of /tmp/lovemrtrump, to retailer stolen information, copies macOS Keychain recordsdata for credential theft, and deploys pretend authentication prompts to seize consumer passwords.
It additional targets desktop cryptocurrency wallets like Electrum, Coinomi, and Exodus, alongside browser information from Chrome, Firefox, and Safari, extracting non-public keys, seed phrases, session tokens, and private recordsdata from Desktop and Paperwork folders.
The stolen information is then compressed right into a ZIP file (out.zip) and exfiltrated by way of a curl POST request to attacker-controlled servers, with persistent retry mechanisms making certain supply even underneath intermittent community situations.
Odyssey Stealer, a rebranded evolution of Poseidon Stealer and a fork of the AMOS Stealer, demonstrates superior capabilities within the macOS malware-as-a-service ecosystem.
Its management panel provides attackers a structured interface to handle contaminated units, customise malware builds, and hijack browser classes utilizing stolen cookies.
The malware’s give attention to over 100 browser extensions, significantly cryptocurrency-related ones like MetaMask, underscores its intent to maximise monetary acquire.
To fight this risk, organizations and people should undertake sturdy endpoint safety options, implement risk intelligence, and configure firewalls to dam identified malicious IPs and domains.
Steady community monitoring, behavior-based anomaly detection, and safety consciousness coaching are vital to mitigating dangers from such social engineering assaults.
As Odyssey Stealer continues to evolve underneath the suspected upkeep of “Rodrigo,” a key determine behind Poseidon and AMOS, vigilance and adaptive defenses stay paramount.
Indicators of Compromise (IoC)
| Indicator | Remarks |
|---|---|
| appmacosx[.]com | Malicious area |
| financementure[.]com | Malicious area |
| cryptoinfo-news[.]com | Malicious area |
| odyssey1[.]to | Odyssey C2 Panel |
| 45[.]135.232.33 | Odyssey C2 Panel |
| a0bdf6f602af5efea0fd96e659ac553e0e23362d2da6aecb13770256a254ef55 | Apple Script |
.png
)