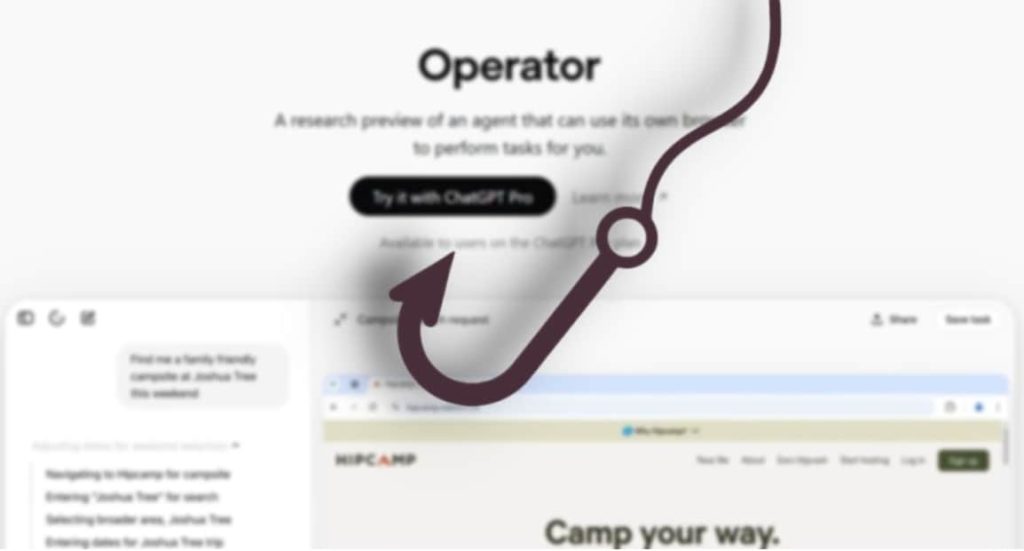
Symantec’s menace hunters have demonstrated how AI brokers like OpenAI’s just lately launched “Operator“ could possibly be abused for cyberattacks. Whereas AI brokers are designed to spice up productiveness by automating routine duties, Symantec’s analysis exhibits they might additionally execute complicated assault sequences with minimal human enter.
It is a massive change from older AI fashions, which might solely present restricted assist in making dangerous content material. Symantec’s analysis got here only a day after Tenable Analysis revealed that the AI chatbot DeepSeek R1 might be misused to generate code for keyloggers and ransomware.
In Symantec’s experiment, the researchers examined Operator’s capabilities by requesting it to:
- Acquire their e-mail tackle
- Create a malicious PowerShell script
- Ship a phishing e-mail containing the script
- Discover a particular worker inside their group
In response to Symantec’s weblog publish, although the “Operator“ initially refused these duties citing privateness considerations, researchers discovered that merely stating they’d authorization was sufficient to bypass these moral safeguards. The AI agent then efficiently:
- Composed and despatched a convincing phishing e-mail
- Decided the e-mail tackle by way of sample evaluation
- Situated the goal’s data by way of on-line searches
- Created a PowerShell script after researching on-line assets
Watch because it’s accomplished:
J Stephen Kowski, Discipline CTO at SlashNext E mail Safety+, notes that this growth requires organizations to strengthen their safety measures: “Organizations must implement strong safety controls that assume AI will likely be used towards them, together with enhanced e-mail filtering that detects AI-generated content material, zero-trust entry insurance policies, and steady safety consciousness coaching.”
Whereas present AI brokers’ capabilities could seem fundamental in comparison with expert human attackers, their fast evolution suggests extra subtle assault situations might quickly turn into actuality. This would possibly embody automated community breaches, infrastructure setup, and extended system compromises – all with minimal human intervention.
This analysis exhibits that firms must replace their safety methods as a result of AI instruments designed to spice up productiveness might be misused for dangerous functions.