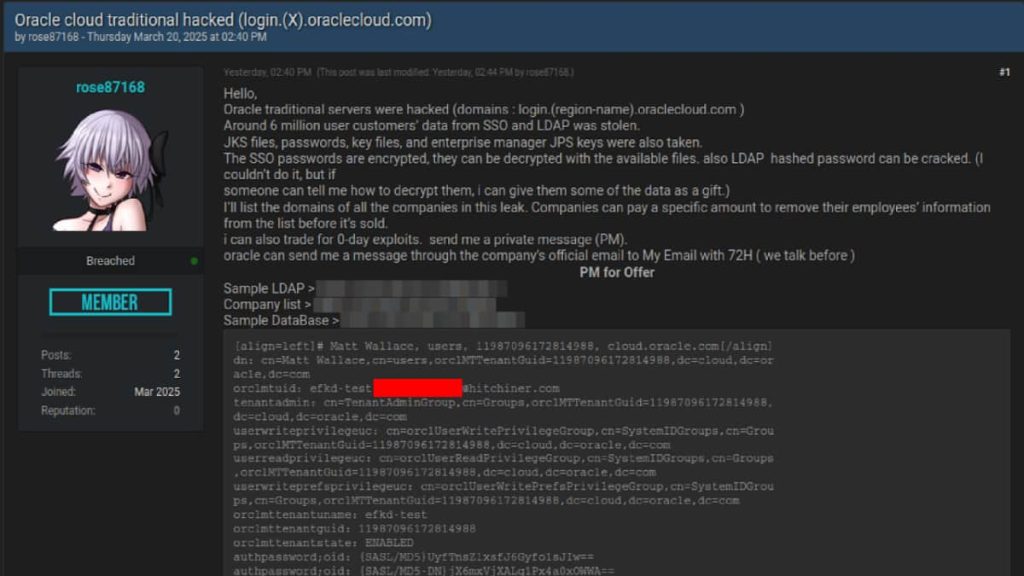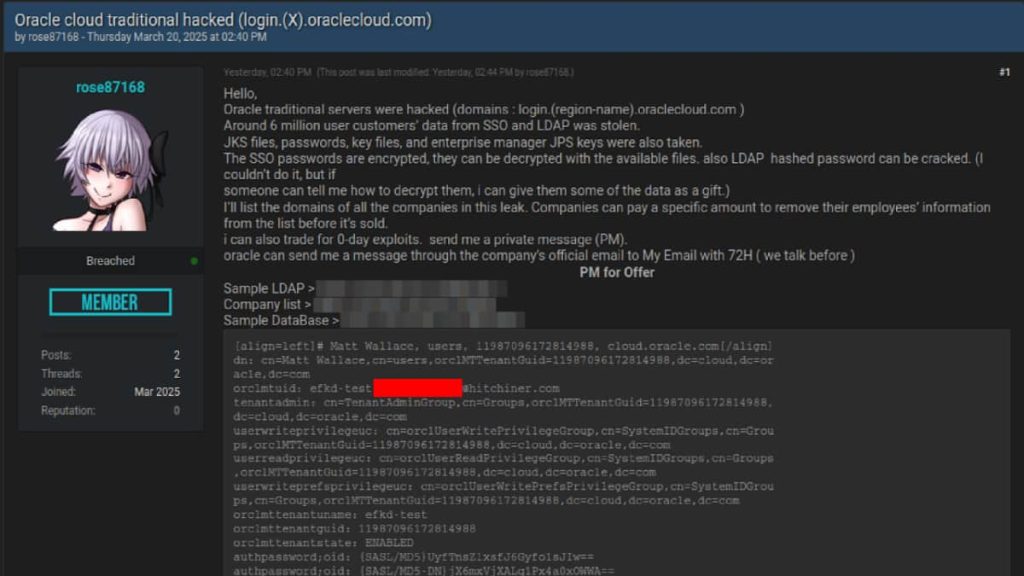
A latest investigation by CloudSEK’s XVigil platform has uncovered a cyberattack focusing on Oracle Cloud, ensuing within the exfiltration of six million data and doubtlessly affecting over 140,000 tenants. Reportedly, a risk actor, recognized as ‘rose87168,’ perpetrated this assault that concerned the theft of delicate knowledge, together with JKS information, encrypted SSO passwords, key information, and enterprise supervisor JPS keys, which are actually being bought on Breach Boards and different darkish internet boards.
The attacker, energetic since January 2025, claims to have compromised a subdomain login.us2.oraclecloud.com, which has since been taken down. This subdomain was discovered to be internet hosting Oracle Fusion Middleware 11G, as evidenced by a Wayback Machine seize from February 17, 2025. They’re demanding ransom funds from affected tenants for the removing of their knowledge and have even supplied incentives for help in decrypting the stolen SSO and LDAP passwords.
CloudSEK’s evaluation signifies that the risk actor could have compromised a weak model of Oracle Cloud servers, doubtlessly leveraging an older flaw, CVE-2021-35587, which impacts Oracle Fusion Middleware (OpenSSO Agent) with the next recognized because the impacted variations:
- 11.1.2.3.0
- 12.2.1.3.0
- 12.2.1.4.0
This CVE, added to the CISA KEV catalogue in December 2022, permits unauthenticated attackers to compromise Oracle Entry Supervisor, doubtlessly main to a whole takeover. This aligns with the kind of knowledge exfiltrated and shared by the attacker. Its exploitation might permit attackers to achieve preliminary entry to the surroundings after which transfer laterally throughout the Oracle Cloud surroundings to entry different methods and knowledge. Additional investigation revealed that the Oracle Fusion Middleware server was final up to date round September 27, 2014, indicating outdated software program.
“Because of lack of patch administration practices and/or insecure coding, the vulnerability in Oracle Fusion Middleware was exploited by the risk actor. This simply exploitable vulnerability permits an unauthenticated attacker with community entry by way of HTTP to compromise Oracle Entry Supervisor,” CloudSEK researchers famous within the weblog put up shared solely with Hackread.com.
Nonetheless, Oracle has issued a press release denying any breach of its cloud infrastructure. “There was no breach of Oracle Cloud. The revealed credentials are usually not for the Oracle Cloud. No Oracle Cloud clients skilled a breach or misplaced any knowledge,” Oracle said in response to the experiences. This instantly contradicts CloudSEK’s findings and the attacker’s claims.
Nonetheless, if it occurred the breach’s impression may very well be substantial because the publicity of a whopping six million data raises the danger of unauthorized entry and company espionage. The exfiltration of JKS information is most regarding as these comprise cryptographic keys, which may very well be used to decrypt delicate knowledge or acquire entry to different methods throughout the affected organizations. Furthermore, the compromise of encrypted SSO and LDAP passwords might result in additional breaches throughout Oracle Cloud environments. The usage of a zero-day vulnerability additionally raises considerations concerning the general safety of Oracle Cloud.
CloudSEK recommends quick credential rotation, thorough incident response and forensics, steady risk intelligence monitoring, and engagement with Oracle Safety for verification and mitigation. In addition they advise strengthening entry controls to forestall future incidents.