Creating Royalty-Free Background Music with AI Background music is important in setting the fitting temper for any...
Samuelwornop
A affected person’s loss of life has been formally related to a cyber assault carried out by...
At Broadcom’s Spark VSM Summit—“VSM evolution meets AI revolution”—SD Occasions sits with VSM head Jean Louis Vignaud to discover...
[{“model”: “blogsurvey.survey”, “pk”: 9, “fields”: {“name”: “AA – Google AI product use – I/O”, “survey_id”: “aa-google-ai-product-use-io_250519”, “scroll_depth_trigger”:...
The sixth annual Sophos State of Ransomware report gives contemporary insights into the components that led organizations...
Leveraging the strengths of two world-class analysis establishments, MIT and Mass Basic Brigham (MGB) just lately celebrated...
ESET Analysis Menace Studies A view of the H1 2025 menace panorama as seen by ESET telemetry...
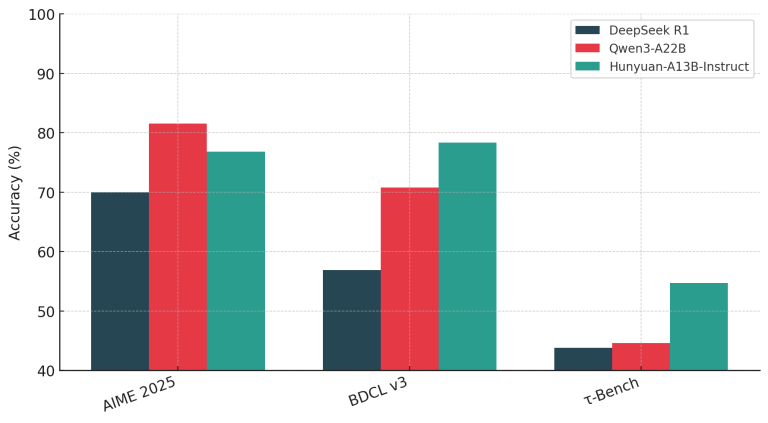
Tencent’s Hunyuan staff has launched Hunyuan-A13B, a brand new open-source giant language mannequin constructed on a sparse...
Writing a classy pc program typically requires plenty of detailed information. If we do that in Java,...
The U.S. Federal Bureau of Investigation (FBI) has revealed that it has noticed the infamous cybercrime group...