Safety researchers efficiently illustrated important vulnerabilities throughout a number of platforms on the primary day of Pwn2Own...
Cybersecurity
The trendy enterprise surroundings exposes organizations to a variety of challenges that have an effect on enterprise...
There may be some huge cash in cyberattacks like ransomware, and sadly for organizations of all sizes,...
Microsoft on Tuesday launched 71 patches affecting 14 product households. Six of the addressed points, 5 involving...
Ever puzzled why a lie can unfold sooner than the reality? Tune in for an insightful have...
Might 13, 2025Ravie LakshmananVulnerability / Menace Intelligence A not too long ago disclosed vital safety flaw impacting...
Cybersecurity Spending , Authorities , Trade Particular Analysts Warn White Home IT Plan Might Battle With Deregulation...
Sophos Managed Detection and Response (MDR) in September 2024, the infamous Lumma Stealer malware has developed with...
Was AI in your RSAC Convention 2025 bingo card? To nobody’s shock, it was the subject...
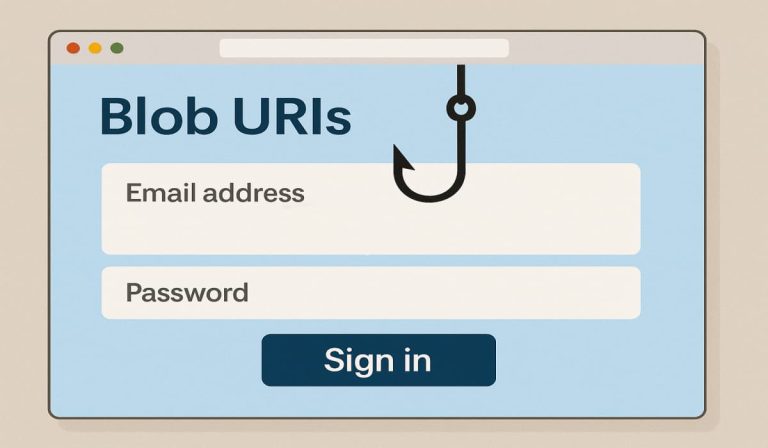
Cofense Intelligence reveals a novel phishing method utilizing blob URIs to create native faux login pages, bypassing...