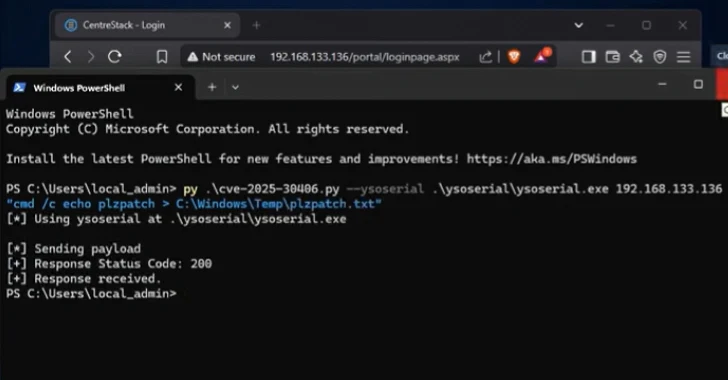
Apr 15, 2025Ravie LakshmananVulnerability / Endpoint Safety A not too long ago disclosed safety flaw in Gladinet...
Cybersecurity
E mail Safety & Safety , Fraud Administration & Cybercrime At-Bay Cyber Insurance coverage Claims Report Finds...
Microsoft in the present day launched updates to plug no less than 121 safety holes in its...
Cybercriminals are more and more exploiting search engine marketing (search engine marketing) strategies and paid commercials to...
Trade surveys counsel that, whereas the variety of ransomware assaults continues to rise, companies aren’t paying...
Organisations demand uncompromising safety towards as we speak’s most urgent threats whereas making certain minimal disruption to...
Russian APT group Storm-2372 employs machine code phishing to bypass Multi-Issue Authentication (MFA). Targets embody authorities, know-how,...
Microsoft on Tuesday launched 135 patches affecting 19 product households. Ten of the addressed points, all distant...
Right here’s tips on how to keep away from being hit by fraudulent web sites that scammers...
What are IABs? Preliminary Entry Brokers (IABs) focus on gaining unauthorized entry into pc programs and networks,...