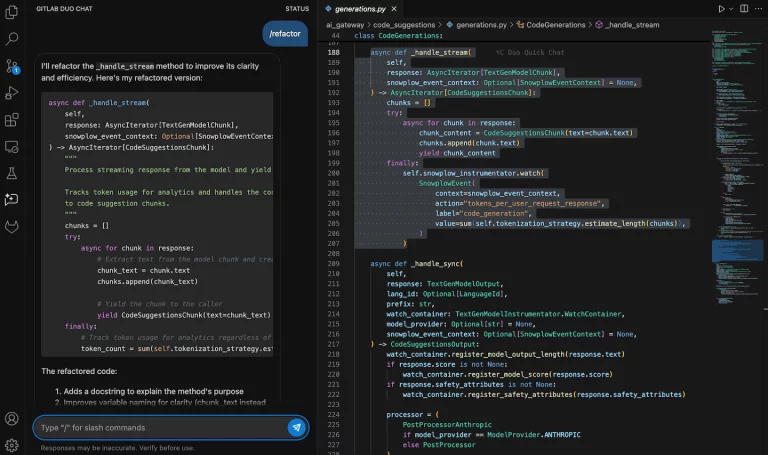
GitLab has introduced the newest model of its platform, incorporating extra AI capabilities from Duo, the corporate’s...
All of us depart traces behind: emails, textual content messages, pictures, voice notes. However what when you...
In a daring leap ahead for semiconductor expertise, Cognichip has launched out of stealth with $33 million...
Knowledge is in every single place and transferring sooner than ever earlier than. If you’re processing logs...
Our strategy to analyzing and mitigating future dangers posed by superior AI fashions Google DeepMind has persistently...
The trendy enterprise surroundings exposes organizations to a variety of challenges that have an effect on enterprise...
The underground world of making and streaming Tremendous Mario World-based ROM hacks continues to realize recognition. This...
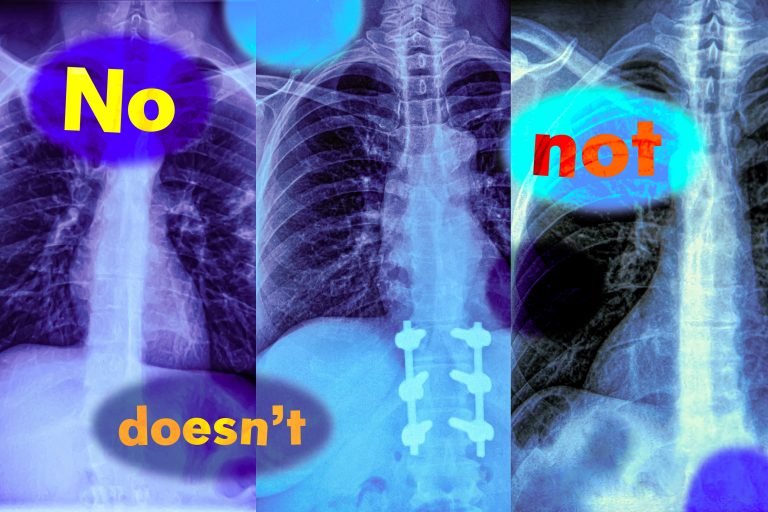
Think about a radiologist analyzing a chest X-ray from a brand new affected person. She notices the...
There may be some huge cash in cyberattacks like ransomware, and sadly for organizations of all sizes,...
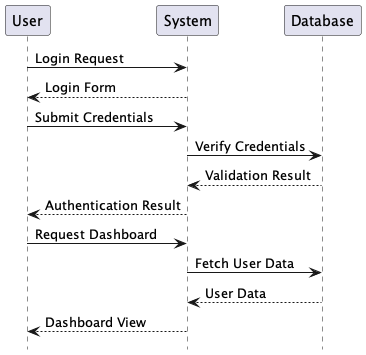
Instruments that deal with diagrams as code, corresponding to PlantUML, are invaluable for speaking complicated system habits....